Introduction to Android Decompilation
Due to work needs, I have learned about decompilation and gained some insights. Here is a summary.

What is Decompilation
APP development involves packaging project code into an APP. For Android, it is an APK package, which is finally installed on the user’s phone through the store or other channels. Decompilation is the process of reverse engineering the APP package to retrieve all the original resources, such as project code.
Is it feasible for Android and iOS?
iOS is a closed environment, so the feasibility is almost zero unless there is a significant investment; you can consider it as zero. Android still has some feasibility, although most current apps have code obfuscation and security reinforcements.
Decompilation Process
The decompilation discussed here is for Android.
Environment Preparation
- JAVA environment - recommended 1.8+
- IDE, recommended
IntelliJ IDEAorAndroid Studio - Unix environment, recommended
Mac, Ubuntu
Decompilation Tools
Tried some online tools decompileandroid, jadx, AndroidDecompiler,
and compared and recommended jadx. Below is a basic introduction to using jadx.
Getting Started
Download ZIP Package
Website: click here, download the latest zip package, and make sure not to choose the source code.
Environment Variables
Different platforms have different configurations.
For example, on Mac, I configured it in cat ~/.bash_profile for user-level environment variables. To take effect immediately, execute source ~/.bash_profile.
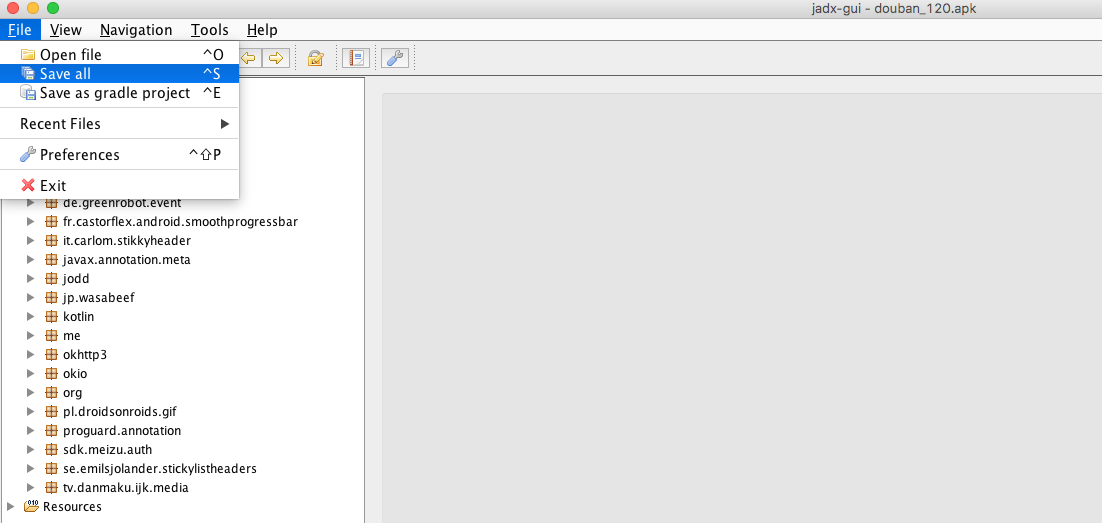
Run Decompilation Tool
# Run the decompilation GUI tool
jadx-gui
Click File—Open File, select the target APK, and wait for the tool to execute automatically. You will see that the tool successfully decompiles the project. You can choose to save all files to a certain place.
Open the Project
The figure shows the project CODE decompiled from a certain app.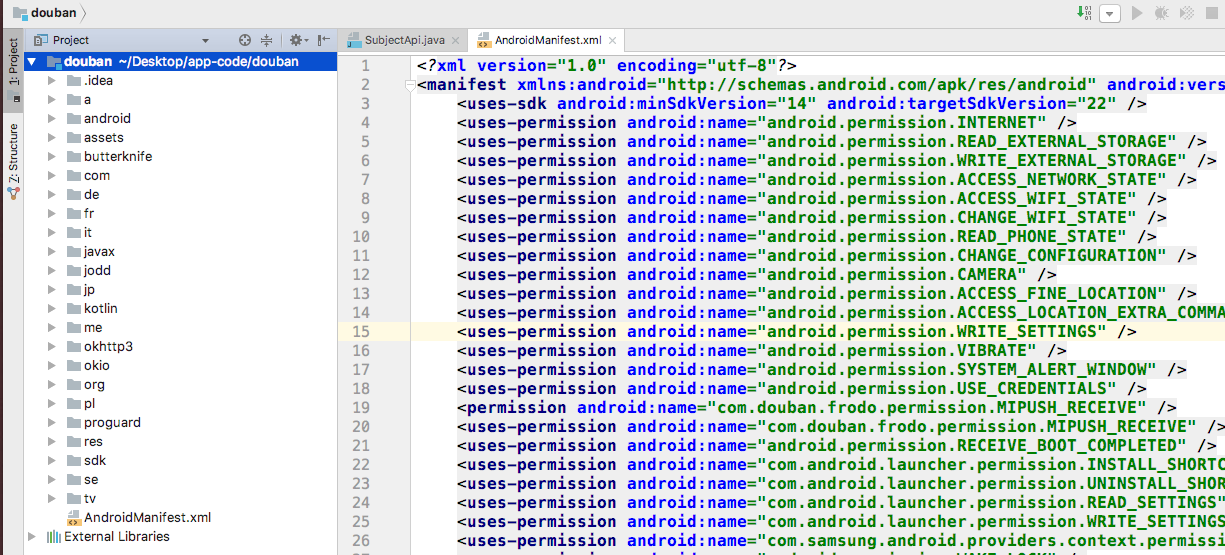
Analyze CODE
This depends on personal skills. Having learned JAVA and Android will help a lot.
Beyond the Code
Besides the decompiled project code, you need to consider two points:
Play with the APP
It will be much easier to find the corresponding Activity and other libraries in the CODE through specific app operations, such as the post button.
Set up an Emulator, Proxy Network, and Capture Packets
Apart from the APP itself, the APP needs to interact with the server. Therefore, using tools like Fiddler to capture packets for analysis can provide interface information and verify certain assumptions. Most current HTTP requests are encrypted, i.e., HTTPS, which requires certificates to resolve. It is recommended to check relevant information.
At the end
Currently, in Android development, code obfuscation is done during packaging. So, even after shelling and decompiling, it doesn’t completely reveal the project’s situation, but it generally doesn’t affect readability. In fact, decompiling some excellent apps, reading others’ code, and understanding their overall design is a great way to learn.
- The front end is inherently transparent, so decompiling to learn is good. Do not directly steal others’ work, which needs to be noted.