Adding HTTPS has become the norm. Modern Chrome flags plaintext sites as “Not secure”. Beyond removing that warning, HTTPS genuinely protects data in transit. I used my own site as an example while documenting the configuration.
Let’s Encrypt certificates
Alibaba Cloud used to offer Symantec certificates for free, but that ended. The good news is Let’s Encrypt delivers free SSL certificates. They only last 90 days, but we can automate renewal.
Setup steps
Install acme.sh
curl https://get.acme.sh | sh
NGINX config: expose the challenge path
When issuing a certificate, the CA checks files under .well-known/acme-challenge/. We need that path accessible.
Example for an NGINX container:
- After validation the folder is cleaned up, so you won’t see files sitting there. Keep the path accessible anyway because renewals need it.
location ^~ /.well-known/acme-challenge/ {
alias /var/www/toolkit/.well-known/acme-challenge/;
try_files $uri =404;
}
Issue the certificate
acme.sh --issue -d tool.alanhe.me --webroot /var/www/toolkit
Copy the certs to NGINX
/etc/nginx/sslmay not exist; create it withmkdir /etc/nginx/sslif needed.- The following command installs the certs automatically—no manual copying required.
acme.sh --installcert -d tool.alanhe.me --key-file /etc/nginx/ssl/tool.alanhe.me.key --fullchain-file /etc/nginx/ssl/fullchain.cer --reloadcmd "service nginx force-reload"
If the command completes successfully, wire the certificate into your NGINX config.
NGINX HTTPS config
server {
listen 443 ssl http2 default_server;
listen [::]:443 ssl http2 default_server;
server_name tool.alan.me;
ssl on;
ssl_certificate "/etc/nginx/ssl/fullchain.cer";
ssl_certificate_key "/etc/nginx/ssl/tool.alanhe.me.key";
...
}
Run nginx -t; if it reports OK, reload NGINX and visit https://tool.alanhe.me. You should see the green lock.
Certificate renewals
Installing acme.sh adds a cron job that checks and renews certificates regularly. No manual work needed. Confirm via crontab -e:
16 0 * * * "/root/.acme.sh"/acme.sh --cron --home "/root/.acme.sh" > /dev/null
Final Thoughts
That’s the complete flow. To simplify future deployments (especially when moving servers), I later containerized the setup. Pull the Docker config, run it, and everything is ready. My blog deployment files are here for reference.
HTTPS security, briefly
HTTPS is more secure because it encrypts data. TCP requires a three-way handshake; HTTP over TLS rides on a TLS handshake (adding four more steps: exchanging and confirming secrets). Diagram from Li Bing’s The Working Principles and Practice of the Browser:
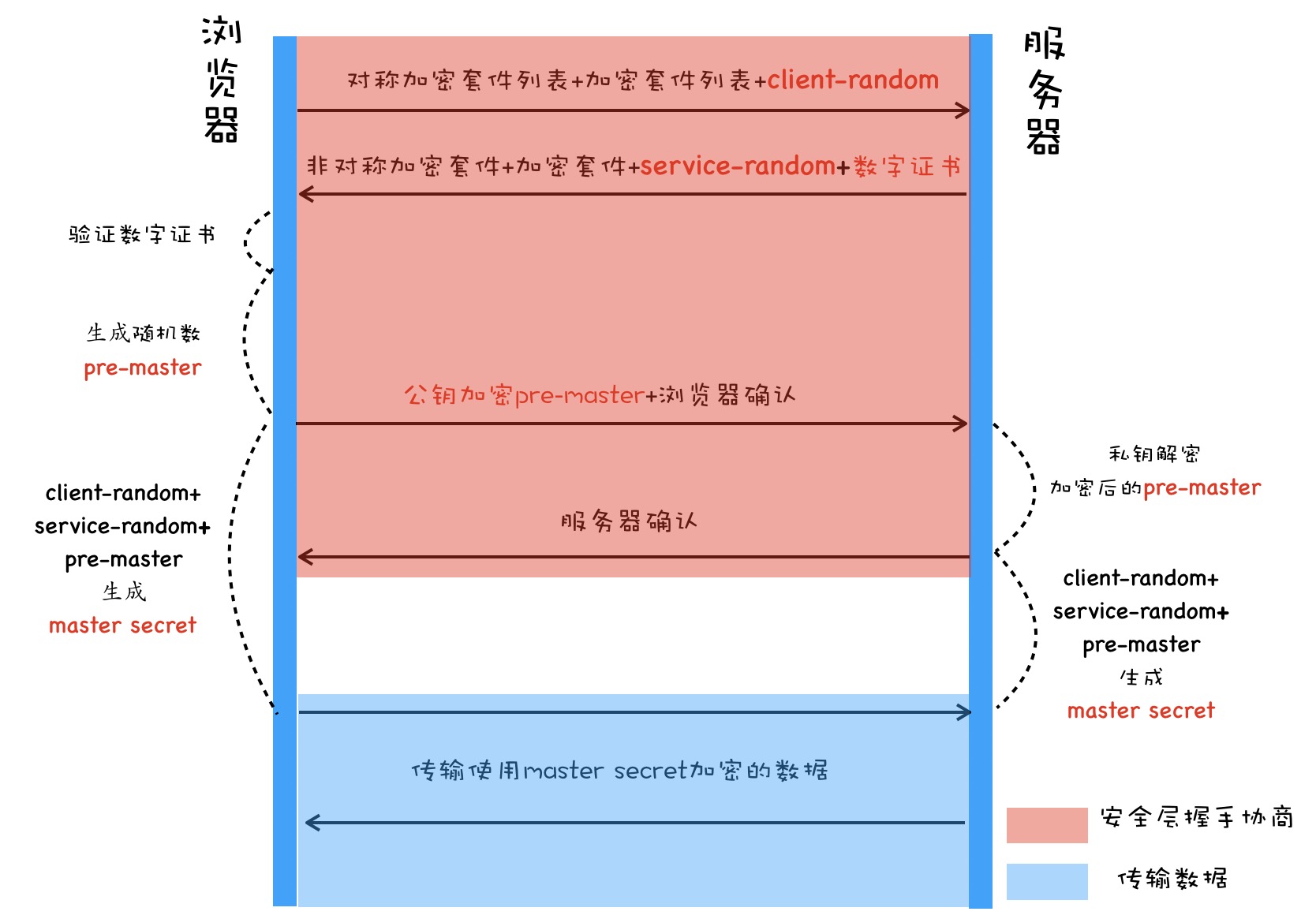
HTTPS is not bulletproof. Certain attacks (e.g., man-in-the-middle) can still succeed under the right conditions, so keep an eye on your overall security posture.

