Recently, I came across news that a Western certificate authority refused to issue HTTPS certificates for Russian domains and even revoked already issued valid certificates.
This made me realize that besides natural expiration, certificates can also be revoked. This was a blind spot for me, so I decided to research and summarize it.
HTTPS Certificate Validity Period
First, it’s important to understand that HTTPS certificates have validity periods and they do expire. This design ensures that website identity information remains current and accurate. Typically, certificates have a maximum validity period of 1 year.
Certificate Revocation List (CRL) Mechanism
The revocation mechanism allows Certificate Authorities (CAs) to revoke certificates that haven’t yet expired. After revocation, when users access the site using a browser, they will be directly alerted that the certificate is invalid.
Regarding the CRL mechanism, here are the key points:
When establishing a secure connection during the first visit to a site, the certificate returned by the site server contains a CRL check address
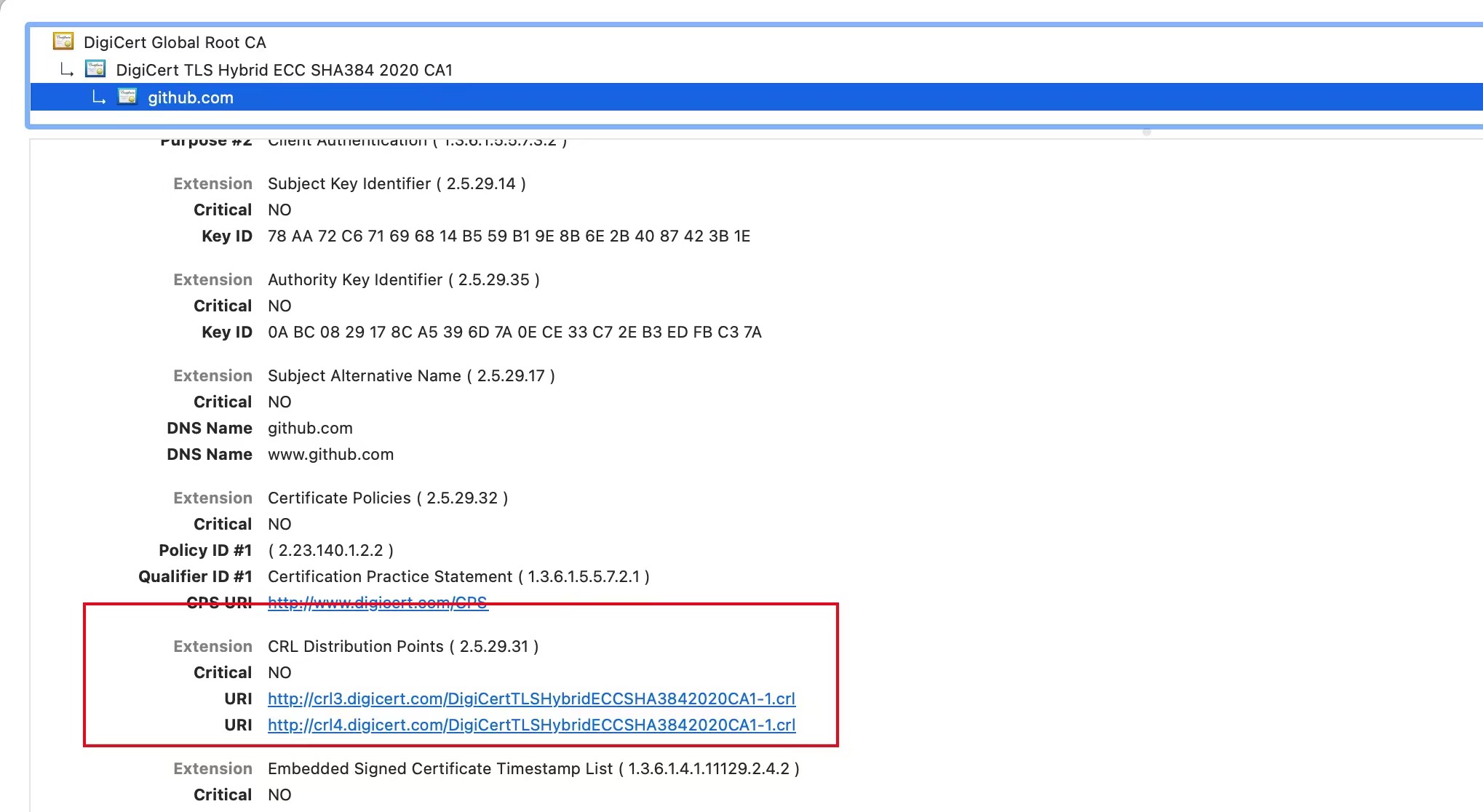
The browser will use the CRL address to check if the certificate is online. If it is, it will continue to check the certificate’s validity period, establish a secure connection, and send encrypted information
The browser stores CRL addresses with a validity period, typically 24 hours. This means that even if a certificate is still within its validity period, if the CA revokes the certificate, the website will report as insecure within at most 24 hours
- For example, in Chrome browser, you can visit
chrome://components/, search for CRL, and manually update it
- For example, in Chrome browser, you can visit
Final Thoughts
Understanding HTTPS certificate revocation is crucial for web security. The CRL mechanism provides an important safety net that allows Certificate Authorities to respond quickly to security incidents by revoking compromised certificates before their natural expiration. While modern browsers have largely transitioned to more efficient mechanisms like OCSP (Online Certificate Status Protocol), the fundamental concept of certificate revocation remains a critical component of the HTTPS ecosystem. It’s important for developers and system administrators to be aware of these mechanisms to ensure proper certificate management and maintain secure web communications.

