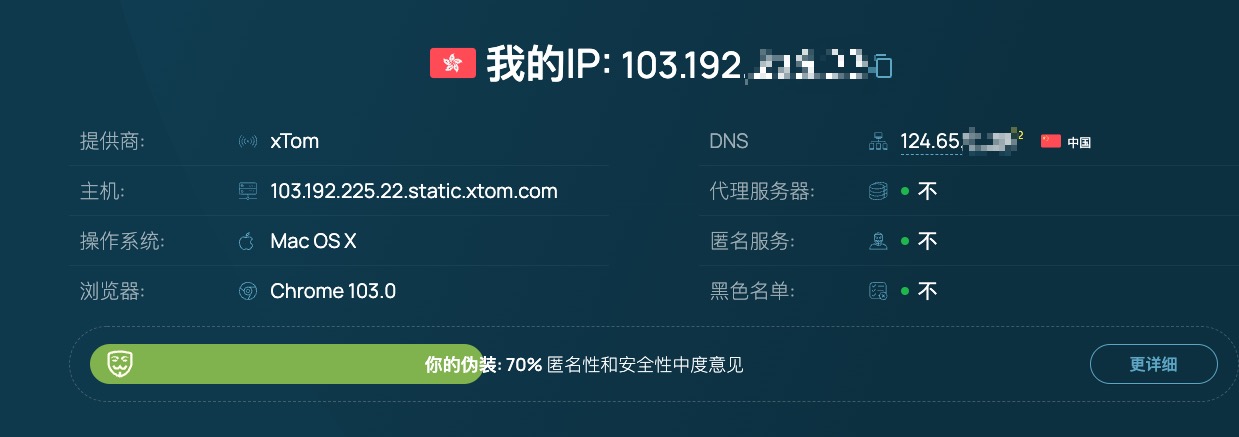
While registering for Spotify I came across whoer and noticed it can detect your DNS server. Curious how that works, I looked into it—here’s the gist.
The whoer page triggers a CSS request like
https://sdvtq1659862.ed.whrq.net/css/null.css?_=1659862263203.The subdomain is randomized and the file doesn’t exist.
Since the DNS answer won’t be cached locally, the resolver walks up the hierarchy and ultimately queries the authoritative DNS for
whrq.net. That DNS server records the randomized subdomain and the source DNS IP for the query.whoer’s backend correlates the recorded subdomain (e.g.,
sdvtq1659862) with the user’s session. The client then issues a request containing that token, and the server returns the detected DNS info.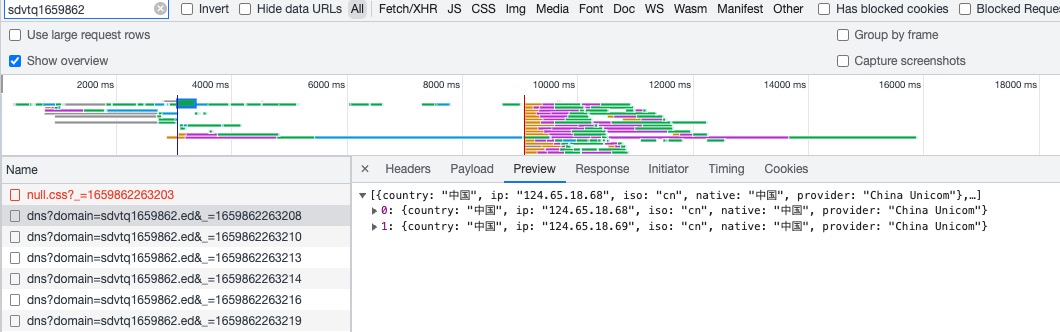
In short, whoer leverages the DNS resolution path to learn your DNS server’s address. Because DNS queries only include the domain, randomized subdomains provide per-user correlation.
Other fields are obtained similarly: OS/browser from the User-Agent, ISP from your IP address.
Done—that’s the core idea.

