Recently while using Wenxin Yiyan (Baidu’s AI), I opened the developer tools and found that it entered a breakpoint in an anonymous function. When clicking to continue execution, the page directly turned into a blank tab. This is clearly an anti-debugging measure. Here I’ll analyze this implementation technique.
Analysis
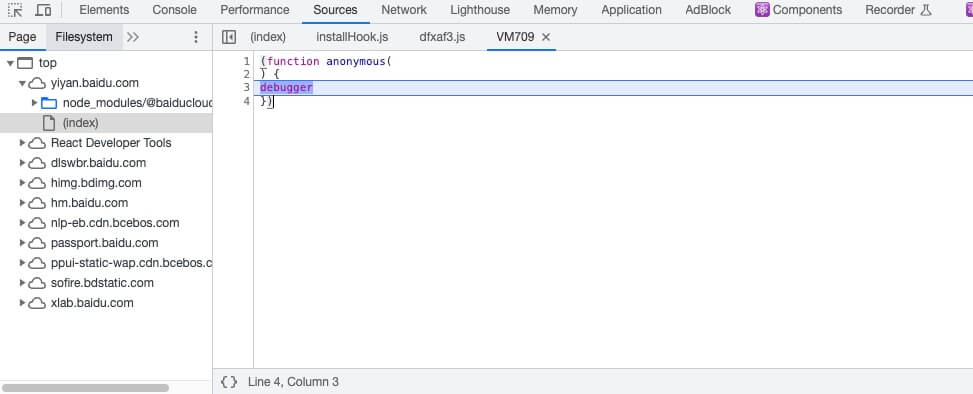
- Examining the call stack at the breakpoint revealed setInterval.
- The tag for the anonymous function is displayed as VM, so the anonymous function containing the breakpoint is code generated by eval or new Function.
- After the breakpoint executes, it runs window.location.replace(“about:blank”);. I couldn’t determine exactly how it detects entering a breakpoint because the code is obfuscated, but one approach is to use time difference detection. When entering a debugger, the logic execution will be significantly delayed, so calculating a time difference can determine if developer tools are open.
Example
(function () {
setInterval(() => {
const startTime = performance.now();
eval('(function() { debugger;})()');
const stopTime = performance.now();
if ((stopTime - startTime) > 1000) {
window.location.replace("about:blank");
}
}, 400)
})()
Xinghua’s Approach
I looked at Xinghua (iFlytek’s AI) and found they also implemented anti-crawling measures, but with a different approach. Xinghua uses the fact that opening developer tools compresses the webpage’s height or width, and detects this difference to make a determination. However, this approach has a drawback - if the developer tools are opened in a separate window, this detection becomes ineffective.
const widthThreshold = window.outerWidth - window.innerWidth > threshold;
const heightThreshold = window.outerHeight - window.innerHeight > threshold;
const orientation = widthThreshold ? 'vertical' : 'horizontal';
Counter-AntiDebug
Having roughly analyzed the implementation methods, the corresponding solutions are quite simple. For Xinghua’s approach, as mentioned earlier, simply using developer tools in a separate window breaks their detection.
For Baidu’s method which uses timers, we can simply override the timer implementation. Using Tampermonkey is recommended:
window.setInterval = function(callback, delay) {
// Here, we simply don't call the original setInterval function, thus blocking all timers
console.log('Blocked a setInterval call with delay ' + delay);
};
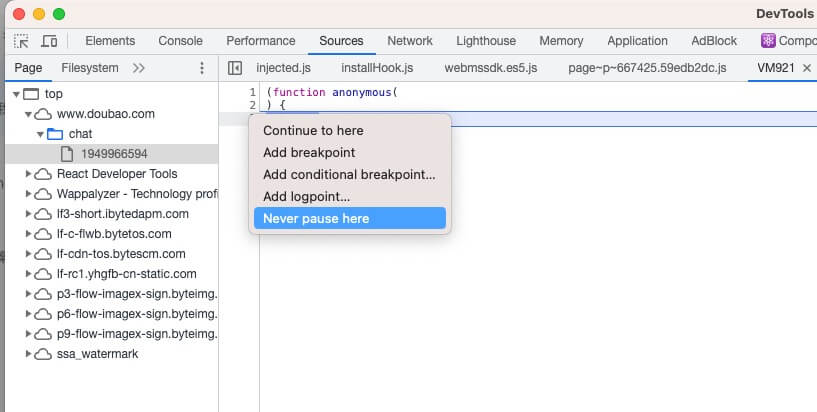
Never Pause Here
Conclusion
- From a purely technical perspective, AntiDebug is interesting - for example, understanding the trigger mechanism of debuggers, learning HACK techniques to detect when developer tools are open, and how to break AntiDebug implementations.
- Setting aside the technical aspects, why are “self-developed” AIs like Baidu and Xinghua afraid of frontend debugging? What are they 100% nervous about?

