The company has jobs that scan R&D projects daily. For Node projects, they promptly alert about component vulnerabilities in packages. When necessary, we need to handle them promptly, as security is no small matter. Here’s a summary of the approach.
Component vulnerabilities generally refer to npm package versions that have records in open-source vulnerability databases, meaning the community has already informed that this version has vulnerabilities, so it’s recommended to upgrade to certain versions.
When receiving such notifications, what needs to be done is to upgrade as soon as possible. Of course, actual operations can be divided into several situations:
- Direct dependencies If the package is a direct dependency, then simply upgrade directly. Just note that if it’s a major version update, consider whether there are usage changes. If so, you need to adjust the calling approach. Of course, more importantly, you need to verify. If the impact is significant, reduce the release speed - safety first.
- Indirect dependencies If the package is an indirect dependency, it’s a bit more troublesome. Priority is to find the direct dependency and upgrade it. If the direct dependency package doesn’t have a new version, you can use resolution to directly control the package version. Of course, here you also need to determine whether the version upgrade is a major version update and what the risk is for the fix release.
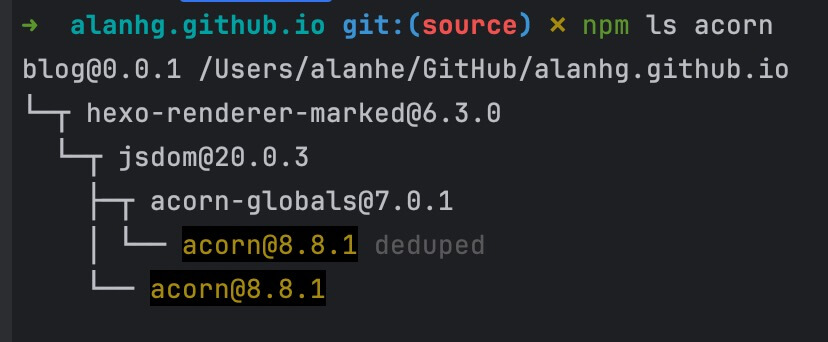
npm ls pkg
Here’s a small tip: using npm ls can quickly determine a package’s dependency tree structure in the project. Based on the version information provided in security reports, you can quickly determine whether it’s a direct or indirect dependency. Even if it’s indirect, you can clearly know which package introduced that version.
npm-check
Whether using npm-check or the built-in interactive update checking in yarn/pnpm, they are excellent ways to query version upgrade information. I recommend using them.
Final Thoughts
done. Security is no small matter. It’s recommended to carefully review each exposed security vulnerability, not just update a version number.

